43 security labels access control
Uniform bucket-level access | Cloud Storage | Google Cloud When you enable uniform bucket-level access on a bucket, Access Control Lists (ACLs) are disabled, and only bucket-level Identity and Access Management (IAM) permissions grant access to that bucket... SharePoint and OneDrive unmanaged device access controls ... Go to Access control in the new SharePoint admin center, and sign in with an account that has admin permissions for your organization. Note If you have Office 365 operated by 21Vianet (China), sign in to the Microsoft 365 admin center, then browse to the SharePoint admin center and open the Access control page. Select Unmanaged devices.
13 Tips to Own SaaS Security - A Complete Guide By following the below security practices, you can leverage the powerful features and advantages of SaaS without worrying about security. 1. End-to-end data encryption This means that all kinds of interaction between server and user happens over SSL connections and are encrypted. However, end-to-end encryption should also exist for data storage.

Security labels access control
Google Play Now Shows How Apps Will Use Your Data - CNET The Google Play Store has a new section meant to help protect your data. Google launched a "Data safety" section in its Play app store on Tuesday. The feature is meant to show people safety and ... Pandemic Rules: What's Different In Your Facilities Today? Facilities management has been heavily impacted by the pandemic. Share your experience with some of the most important topics that have impacted facilities management and see how your experience compares to that of your peers. 1. CyberRes Blog | Micro Focus Community In this week's Reimagining Cyber podcast, we talk to Bob Almond, Chief Operating Officer of Full Armor Corporation. Bob has watched the industry evolve to where people now work from anywhere and need to have access to the resources they need to get their jobs done. Bob discusses reining in the complexities of AD group policies to enable ...
Security labels access control. How-To: Apply access control list configuration for ... An access control policy is specified in configuration and be applied to Dapr sidecar for the called application. Example access policies are shown below and access to the called app is based on the matched policy action. You can provide a default global action for all calling applications and if no access control policy is specified, the ... Implement NIST IoT cybersecurity guidelines early ... The NIST recommendations outline cybersecurity criteria for an IoT product labeling program that would include label criteria and design considerations for user education and conformity assessment. The program would provide clear indication of whether or not an IoT product or software package has met a set of specified cybersecurity requirements. › whitepapers › security-labelsAccess Control using Security Labels & Security Clearance Security Labels and Security Clearance provides a mechanism for controlling access to information that works well for large numbers of users. It can be an effective approach for access control in organizations that do not use non-electronic security labels. The following diagram shows the translation of the earlier example into electronic form. Cyber Security Specialist at Resource Label Group, Inc ... assess & address these various vulnerabilities in the networkthis role will also address any attempted attacks and intrusions, must be able to recognize a potential threat or attempted breach and must be able to address it accordinglythe professional should suggest security measures to act on and will design various strategies & defensive systems …
Plan an Azure Active Directory B2B collaboration ... Resource tenant controls all access and authorization of guest users. Can collaborate with any user who has an email address without need for partner infrastructure. No need for IT departments to connect out-of-band to set up access/federation. Guest user access is protected by the same enterprise-grade security as internal users. SELinux is unmanageable; just turn it off if it gets in ... Security-Enhanced Linux (SELinux) is a type of Mandatory Access Control ( MAC) in the Linux kernel. It can prevent software from performing unexpected — such as abusive or malicious actions — on your Linux systems. However, … it's also an unmanageable mess, and I have a much greater understanding of why people recommend that people disable it. Verkada Wins Coveted Red Dot and iF Design Awards for ... Verkada Access Control seamlessly combines easy-to-use hardware and cloud-based software to provide a modern, scalable approach to physical security. With access control, organizations can add an... Microsoft Virtual Training Days - Security Learn how to harness powerful Microsoft security capabilities to keep your company's information and remote access secure and protected against threats. Take control of your organization's digital security needs with defenses built for the modern workforce. Upcoming Online Sessions Security, Compliance, and Identity Fundamentals
› docs › enLabel-based access control (LBAC) overview Label-based access control (LBAC) greatly increases the control you have over who can access your data. LBAC lets you decide exactly who has write access and who has read access to individual rows and individual columns. What LBAC does The LBAC capability is very configurable and can be tailored to match your particular security environment. Create a security plan for external access to Azure Active ... Entitlement Management Access Packages enable you to create and delegate management of packages of Applications, Groups, Teams, SharePoint sites, and other resources to which you can grant access. Conditional Access policies can be applied to up to 250 applications with the same access requirements. Security Officer-Access Control Job Council Bluffs Iowa ... Allied Universal - [Security Officer / Security Guard] As an Access Control Security Guard at Allied Universal, you'll: Fingerprint, create badges, activate, deactivate , and respond to employee termination emails; Display excellent customer service skills and proficiency in Microsoft Office ; Be detail-orientated and a problem solver. Pod Security Policies - Kubernetes A Pod Security Policy is a cluster-level resource that controls security sensitive aspects of the pod specification. The PodSecurityPolicy objects define a set of conditions that a pod must run with in order to be accepted into the system, as well as defaults for the related fields. They allow an administrator to control the following:
Integrate MDM and UEM Servers with Cisco ISE - Integrate ... You can then use the device attributes to create Access Control Lists (ACLs) and authorization policies to enable network access control. This document details the configurations that you must perform in your endpoint management servers to integrate these servers with Cisco ISE.
Configure a Security Context for a Pod or ... - Kubernetes A security context defines privilege and access control settings for a Pod or Container. Security context settings include, but are not limited to: Discretionary Access Control: Permission to access an object, like a file, is based on user ID (UID) and group ID (GID). Security Enhanced Linux (SELinux): Objects are assigned security labels.
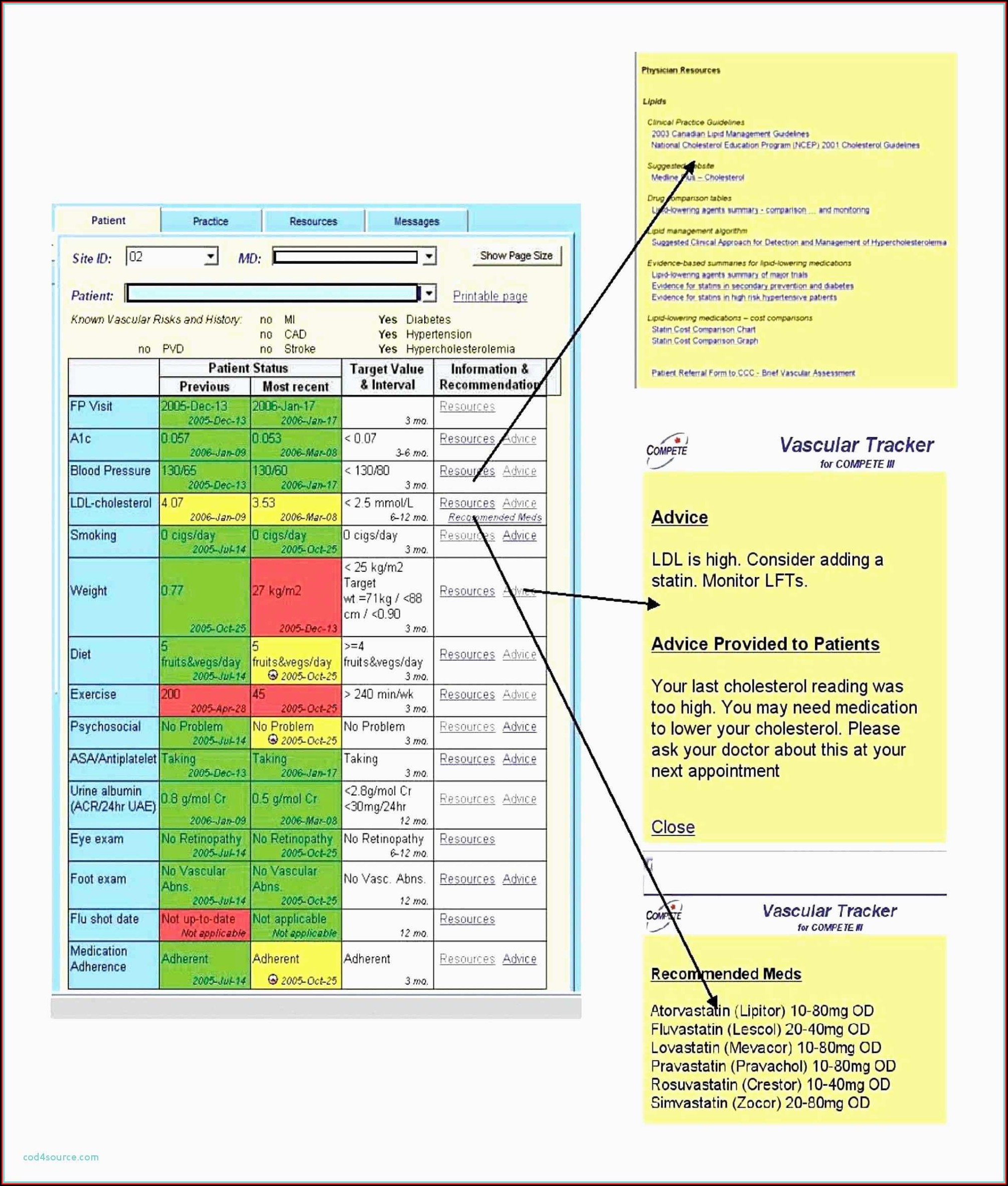
Learn about sensitivity labels - Microsoft Purview ... This label configuration doesn't result in documents or emails being automatically labeled but instead, the label settings protect content by controlling access to the container where content can be stored. These settings include privacy settings, external user access and external sharing, and access from unmanaged devices.
Security Command Center conceptual overview - Google Cloud Security Command Center roles are granted at the organization, folder, or project level. Your ability to view, edit, create, or update findings, assets, and security sources depends on the level...
VPN - Cisco Community VPN Labels AAA (2) Access Control Server (ACS) (1) AnyConnect (5,705) Appliances (1) ATAs and Gateways and Accessories (1) Buying Recommendation (28) Cisco Adaptive Security Appliance (ASA) (21) Cisco Cafe (9) Cisco Cloud Services Router (1) Cisco DNA (2) Cisco DNA Automation (1) Cisco Firepower Device Manager (FDM) (2)
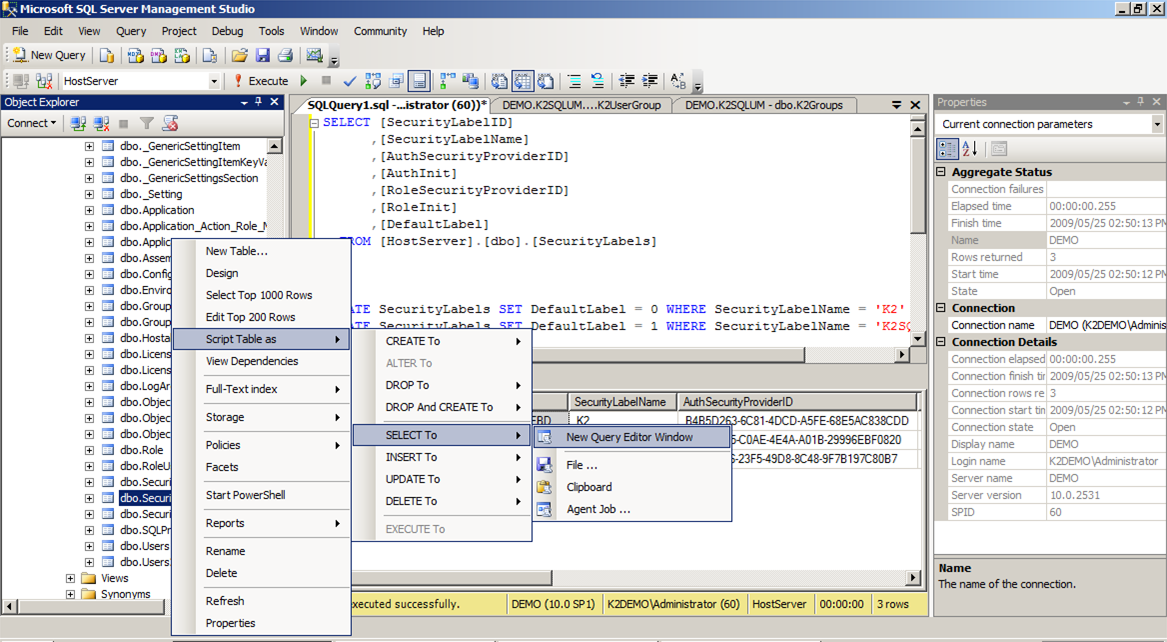
› docs › SSB27U_7Security Labels and Mandatory Access Control (MAC) Security Labels and Mandatory Access Control (MAC) Mandatory Access Control (MAC) is a security policy that governs which subjects can access which objects, and in what way, based upon certain rules. These rules are the “*-property” and the “simple security property.” RACF commands are used to manage MAC for CP commands, DIAGNOSE
This Egg Company Stock Is Surging Along With the Price of ... Revenue growth was driven by a 29% surge in the average selling price the company received for its eggs, along with a 3% increase in sales volume. Net income was $39.5 million, or $0.81 per share ...
Give users access to the Security & Compliance Center ... To verify that you've successfully granted access to the Security & Compliance Center, do either of the following steps: In the Security & Compliance Center, go to Permissions and select the role group. In the details flyout that opens, verify the members of the role group.
Flex Retail Merchandiser Job Council Bluffs Iowa USA,Retail Job in Council Bluffs - Pottawattamie County - IA Iowa - USA , 51503. To Apply. ↓. Tap HERE. Company: Driveline Retail. Full Time, Part Time position. Listed on 2022-04-26. Job specializations: Retail.
Summary of BigQuery data security and governance features ... Introduction to BigQuery column-level security BigQuery provides fine-grained access to sensitive columns using policy tags, or type-based classification, of data. Using BigQuery column-level security, you can create policies that check, at query time, whether a user has proper access. Column-level security: Row-level security
Technology and Support Events and Webinars - Cisco Community Wednesday, April 27, 2022. Networking Software Demo Series: Cisco DNA Center Date and time: April 27, 2022, 10:00 a.m. PT Cisco DNA Center offers a low-risk, lower-cost, incremental approach to adopting network technologies in your branch, campus, and wireless environments. It simplifies and automates the way you communicate with the network ...
Contrasting OMNIQ (OTCMKTS:OMQS) and Allin (OTCMKTS:ALLN ... The company offers computer vision image processing-based solutions using AI technology to deliver data collection, and real time surveillance and monitoring for supply chain management, homeland ...
Focus On: Facility Management Software Wilsonart High Pressure Laminate Products Receive Declare Label. ... In the face of evolving security threats, Policy-Based Access Control (PBAC) might be the Zero Trust physical security solution we've been waiting for. Flexible Focus Shapes New School. In-Depth Case Studies April 27, 2022.
CyberRes Blog | Micro Focus Community In this week's Reimagining Cyber podcast, we talk to Bob Almond, Chief Operating Officer of Full Armor Corporation. Bob has watched the industry evolve to where people now work from anywhere and need to have access to the resources they need to get their jobs done. Bob discusses reining in the complexities of AD group policies to enable ...
Pandemic Rules: What's Different In Your Facilities Today? Facilities management has been heavily impacted by the pandemic. Share your experience with some of the most important topics that have impacted facilities management and see how your experience compares to that of your peers. 1.











Post a Comment for "43 security labels access control"